Why MSPs Should Implement the CIS Controls
There’s often a major disconnect between businesses and their Managed Service Providers (MSPs) over one key issue: cybersecurity.
Many businesses believe their MSPs are covering their cybersecurity needs. But the majority of MSPs have no expertise in managing cybersecurity, instead focusing primarily on providing basic IT solutions that maintain a business’s existing systems. This results in misunderstandings that can leave businesses with major cybersecurity gaps.
When an MSP fails to take a security-first approach to building and maintaining your business’s IT infrastructure, they’re not just putting their contract with your business at risk – they’re putting you and your team’s livelihoods in jeopardy. Suffering a cybersecurity attack can have major consequences for your business, often triggering a series of operational, financial, and legal challenges that even the most robust companies struggle to overcome.
If your MSP isn’t implementing thorough cybersecurity controls across your IT infrastructure, it might be time to start looking for an alternative. In this overview, we’ll explore the importance of taking a security-first approach to IT infrastructure management and explain exactly what that looks like in practice.
Tech Heads is a Managed Service Provider based in Portland, OR. Our MSP solution, ThInc OpsTM provides a security-first MSP experience that fuels operational growth while keeping your infrastructure secure. Contact an advisor today to learn more.
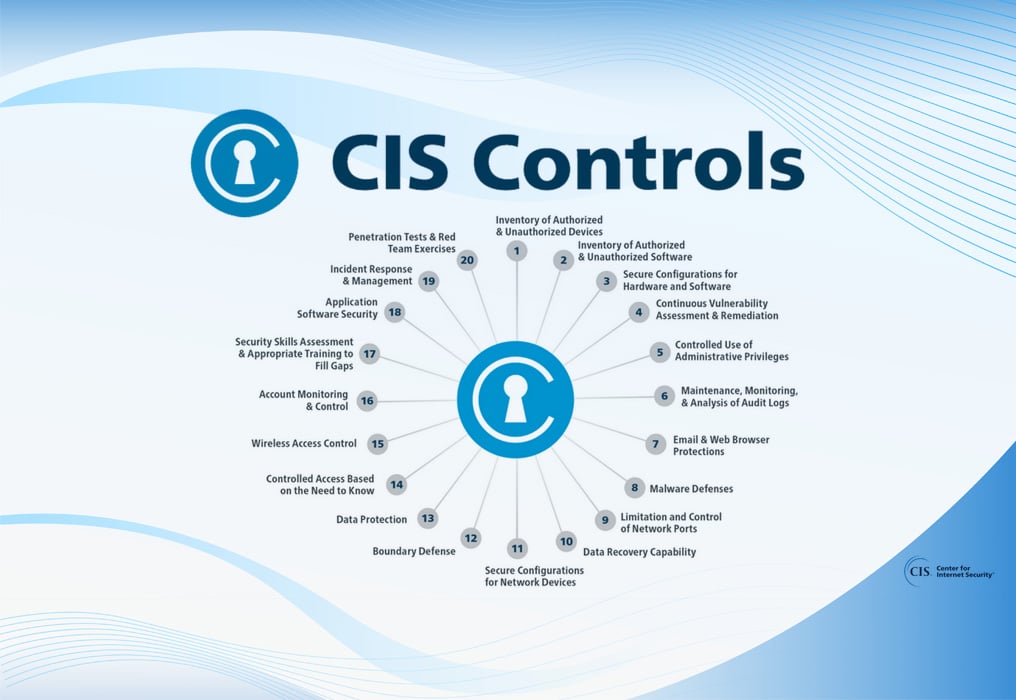
What Are the CIS Controls
The best MSPs base their service architecture on widely-accepted cybersecurity frameworks. Choosing a framework is important to ensure there are neither gaps or overlaps in resource allocation. Chief of these frameworks is the Controls by the Center for Internet Security (CIS), a range of cybersecurity benchmarks developed by the Center for Internet Security.
These controls, which have been developed and iterated over several years, outline a series of areas that organizations (and their IT service providers) should focus on to drive increased levels of security in their organization. Example controls include ensuring a secure configuration of enterprise assets and software as well as proactive network infrastructure management.
We recently broke down all 18 of the CIS Controls in this blog post: CIS Controls v8: Cybersecurity Best Practices
Some MSPs embrace more than one cybersecurity standard. Other popular frameworks include the National Institute of Standards and Technology (NIST) Cybersecurity Framework as well as various ISO frameworks.
The Value of a Security-First Approach to IT Infrastructure
It’s perhaps never been more important for organizations to adopt a security-first approach to managing their IT infrastructure. Recent years have seen a sharp increase in the prevalence of cybersecurity incidents. These risks show no signs of slowing, with the number of cyber attacks growing by 7% in the first quarter of 2023.
With attacks on the rise, it’s vital for businesses to invest in cybersecurity. Too many organizations wait until after a breach to address their cybersecurity strategy – an approach that’s too little, too late, and often winds up costing significantly more. Instead, IT leaders should embrace a proactive approach to cybersecurity.
Proactive IT Infrastructure Management
The best MSPs have a systematic framework that they apply across a variety of different clients. This tried-and-tested strategy is based on robust cybersecurity principles, such as the CIS Controls, and takes a proactive approach toward bringing your IT infrastructure in line with these standards.
Engagements typically start with a cybersecurity assessment. These diagnostic engagements provide a snapshot of your organization’s current level of security, enabling you and your MSP to jointly identify the key priorities that should be addressed as you move forward together. At Tech Heads we have developed a proprietary Cybersecurity Scorecard that maps exactly to the CIS Controls.
By mapping your organization’s current capabilities, you can build a joint security roadmap that outlines how your organization can enhance its security profile. Exactly what these steps will look like depend on your business: it could be replacing older technologies with more modern equivalents or implementing stricter access management controls to key organizational assets.
Transfer of Risk
A business might believe that working with an MSP provides a transfer of cybersecurity risk to an external party, but unless these responsibilities are explicitly stated in the Service Level Agreement (SLA) that’s typically not the case.
If you choose to work with a more security-focused MSP, your business can more effectively transfer this risk. That gives IT leaders and their teams added peace of mind, plus the freedom to channel more of their time and energies toward IT initiatives that help their business operate more effectively.
Access to Accepted Best Practices
Cybersecurity is a fast-moving, ever-evolving discipline. Without the right guidance, it’s challenging for IT leaders to stay on top of all the latest developments and understand how their organization’s IT infrastructure should evolve in line with established best practices.
The right partner acts as a trusted advisor to navigate your business through this complex landscape. They’ll stay abreast of all the best practices so that you don’t have to, routinely updating the various elements of your IT infrastructure to ensure your business remains protected against the latest threats.
Tech Heads: A Security-Focused MSP
Finding an MSP that anchors every element of their service in security isn’t easy. At Tech Heads, security serves as the foundation of our MSP solution. Our MSP services are purpose-built to meet established cybersecurity controls, covering 11 of the 18 CIS Controls.
THInc OpsTM, our Managed IT Service, implements monitoring, alerting, patching, systems maintenance, and password management, ensuring your business has a strong security foundation to build from. In addition, our team also offers end user support, incident support, and endpoint protection, ensuring that your systems maintain functionality and your business can continue to operate in the face of any IT incidents.
It’s this distinct approach to managed IT services that sets us apart from many of our peers. Our team of 25 experts work together to provide secure infrastructure and operations, offering a diverse range of additional services including employee security awareness training, IT consulting, and procurement services.
This comprehensive approach brings a variety of benefits to the organizations we work with, enhancing security, increasing the capacity of existing IT resources, and providing leaders with peace of mind.
Interested in learning more about working with a security-focused MSP? Contact Us Today!
Search
Recent Posts
- Gmail and Apple begin enforcing stricter email requirements for delivery. Are you in compliance?
- Top 10 Reasons Midsize Organizations Use a Co-Managed IT Service Model
- Why MSPs Should Implement the CIS Controls
- A Guide to Evaluating Your Managed Service Provider (MSP)
- How to Find an MSP That’s a Right Fit For Your Organization

